| |||||||
|
Simple WolfSSL Client Side Example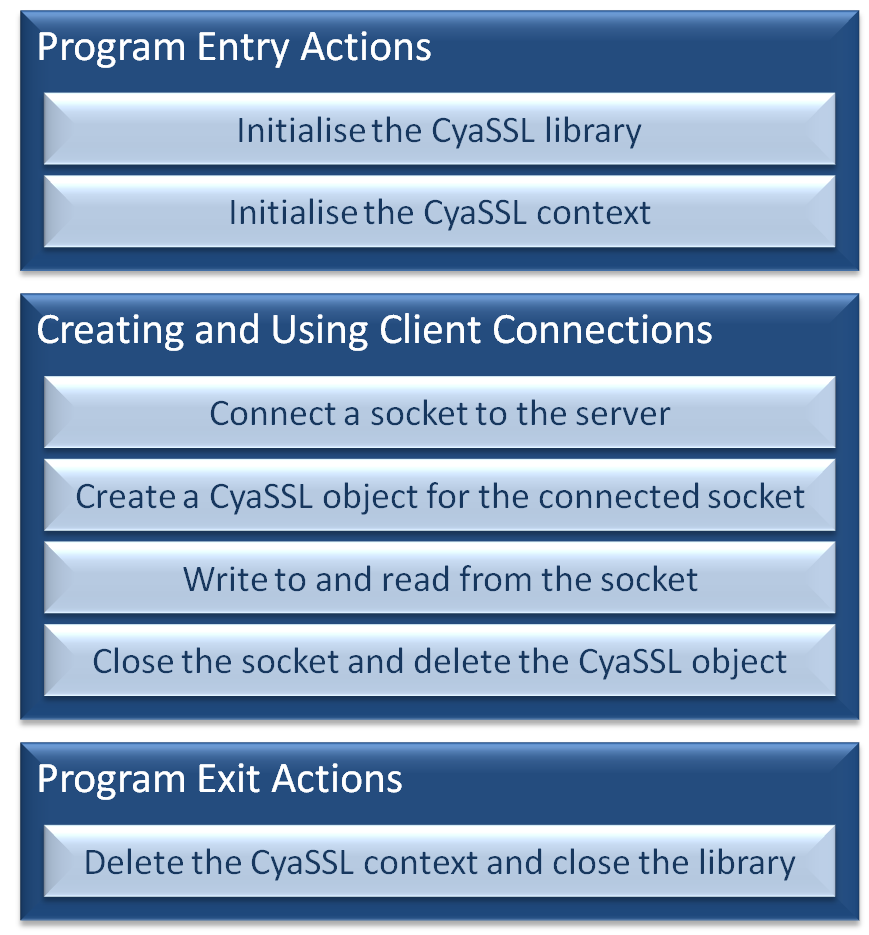
The three steps to using WolfSSL in a client side application
IntroductionThis page describes how, in just a few easy steps, the WolfSSL library can be used to to ensure the security and integrity of a client side networking application.
Header fileswolfssl/ssl.h contains the WolfSSL structures, data definitions, and function prototypes. It must be included in all the source files that use the WolfSSL library.
Initialising the library and creating a WolfSSL contextwolfSSL_Init() prepares the WolfSSL library for use, and must be called before any other WolfSSL API functions.Next, a variable of type WOLFSSL_CTX is required to store context information, and can be created using wolfSSL_CTX_new(). The SSL or TLS protocol to use is specified as the context is created using the function's parameter. Options include SSLv3, TLSv1, TLSv1.1, TLSv1.2, or DTLS. This example demonstrates the TLSv1 client protocol being selected. The values to use to select the other protocol options are listed in the user manual. The final initialisation step is loading a Certificate Authority (CA) into the WolfSSL context. This allows authentication with the server the client will connect to. wolfSSL_CTX_load_verify_locations() is used for this purpose. In the example below, the first function parameter specifies the context into which the CA is loaded, and the second the CA certificate that is used. The third parameter can be used to specify a file path that will be searched for certificates, but in this case the file path is not necessary and so set to 0.
Associating a WolfSSL object with a connected socketEach TCP connection must be associated with a WolfSSL object. WolfSSL objects are created using wolfSSL_new(), and associated with a TCP socket using wolfSSL_set_fd().
Using the socketSecure communication can now be made through the socket by using wolfSSL_write() in place of the standard sockets write() or send() functions, and wolfSSL_read() in place of the standard sockets read() or recv().Note that the first parameter to both wolfSSL_write() and wolfSSL_read() is not the socket descriptor, but the WolfSSL object that is associated with the socket descriptor.
Deleting allocated resourcesWolfSSL API functions that result in dynamic resource allocation have a counterpart function that should be called to free the resource when it is no longer required. The code snippet below shows how the objects created in this small example should be freed.
|


